3DS Server Database Configuration
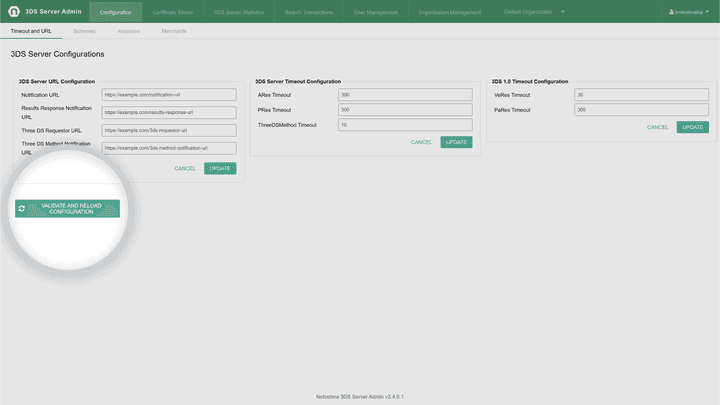
Validate and Reload configuration
It is important to note that for updates that are made to any of the sections below (Timeouts, Schemes, Acquirers, Merchants, Certificates), the button "Validate and Reload configuration" must be pressed, in order for the changes to be loaded and the new configuration activated. You will find the button in the bottom left corner of the configuration pages.
Additionally, please also update the configuration in case a yellow banner appears, notifying that the default configuration has been updated. This way the newest changes from the default organization will be loaded into current configuration.

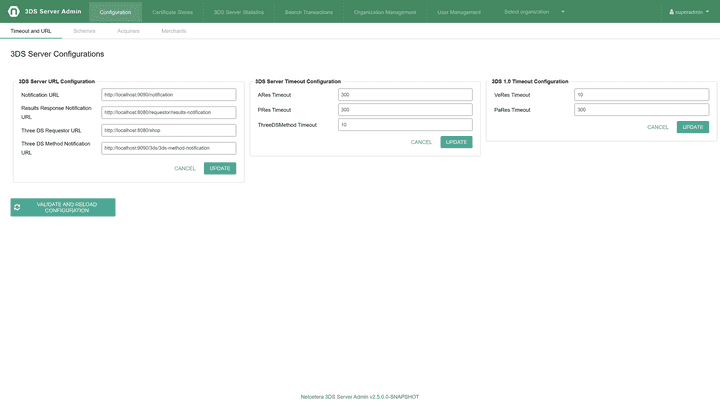
Timeouts and URL configuration
The Timeout and URL tab allows configuration of URLs for communication between the DS, 3DS Server and organization as well as the 3DS Server Timeouts for different message types.
In case of any not configured 3DS Server timeout via the UI, the Admin application will internally resolve default values.
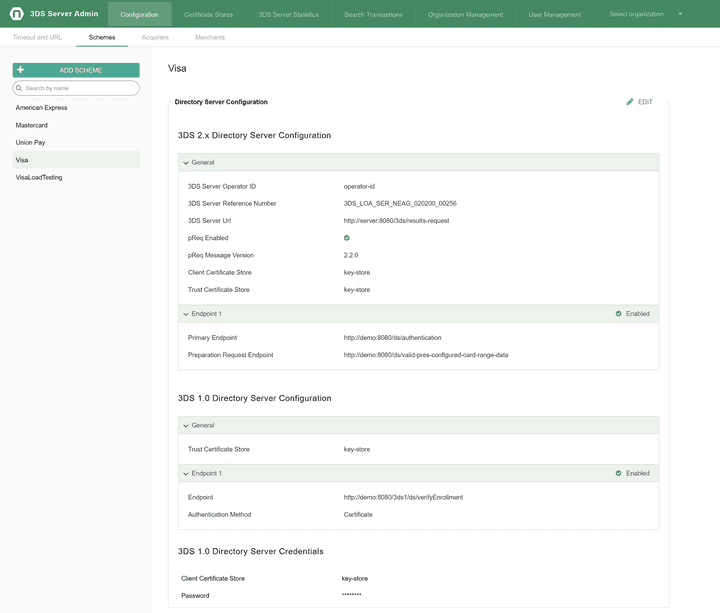
Schemes configuration
The Schemes tab allows configuration of Scheme related information (Scheme ID and DS configuration, including the DS credentials).
Supported scheme configuration naming
All supported scheme configurations should be named accordingly.
- Visa scheme ID: Visa
- MasterCard scheme ID: Mastercard
- American Express scheme ID: American Express
- JCB scheme ID: JCB
- Diners scheme ID: Diners
- MIR scheme ID: Mir
- Cartes Bancaires scheme ID: CB (For Cartes Bancaires, it is recommended to send the scheme ID)
- Union Pay scheme ID: UnionPay (For UnionPay, it is recommended to send the scheme ID)
Acquirers configuration
The Acquirers tab allows configuration of Acquirer related information (Acquirer Name, Acquirer BIN configuration, configuration).
Furthermore, the Acquirer data can also be provided in the payload, instead of having it configured via the Admin UI. For more information, please refer to the example models for AReq (3DS 2.x) and PaReqCreationRequest (3DS 1.0).
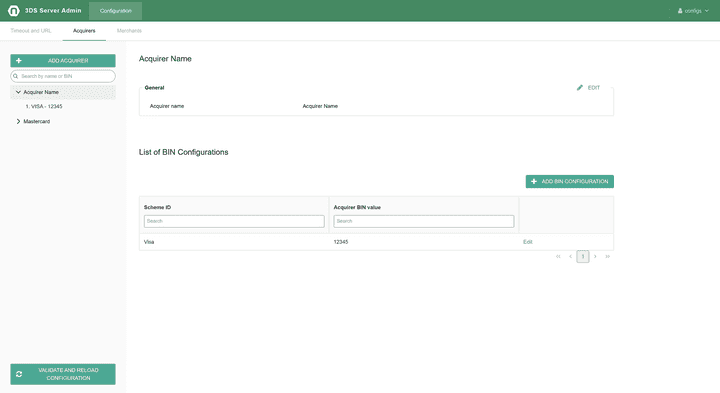
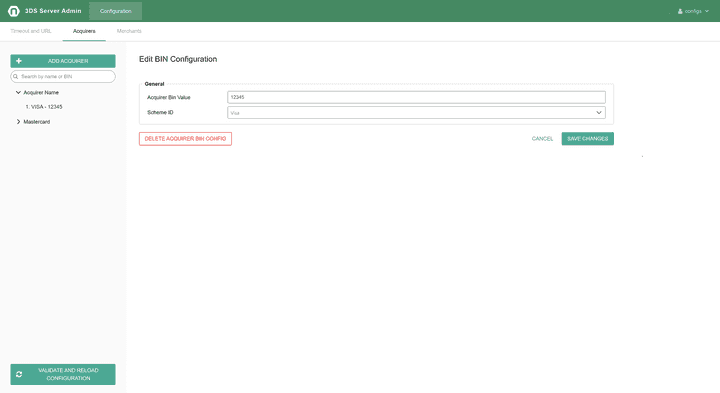
In 3DS 1.0, for some payment schemes the client certificate store shall be set on the level of either AcquirerBin or MerchantAcquirer.
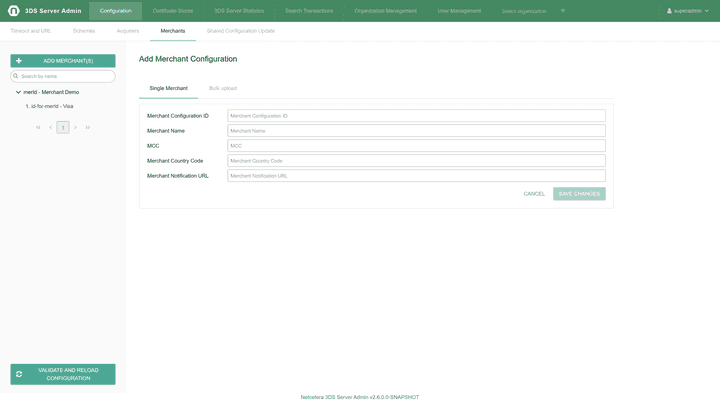
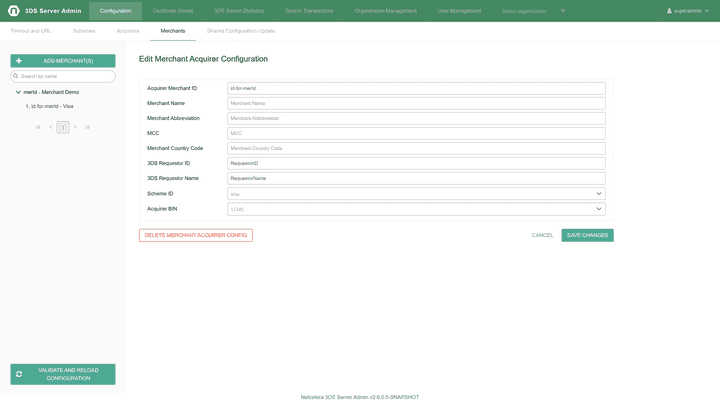
Merchants configuration
The Merchants tab allows configuration of Merchant related information (Merchant Name, Merchant acquirer information).
For adding new Merchant(s) there are two possible options: Adding a single Merchant, Adding Merchants in bulk.
Single Merchant:
Merchants in bulk:
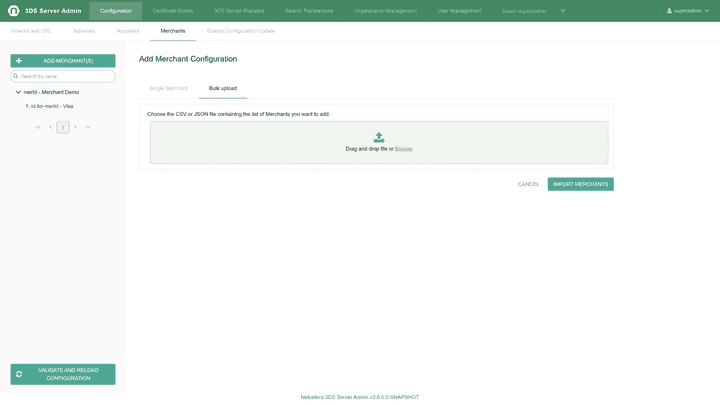
For more information on Adding Merchants in bulk please refer to the Insert Merchants in bulk page.
View Merchant:
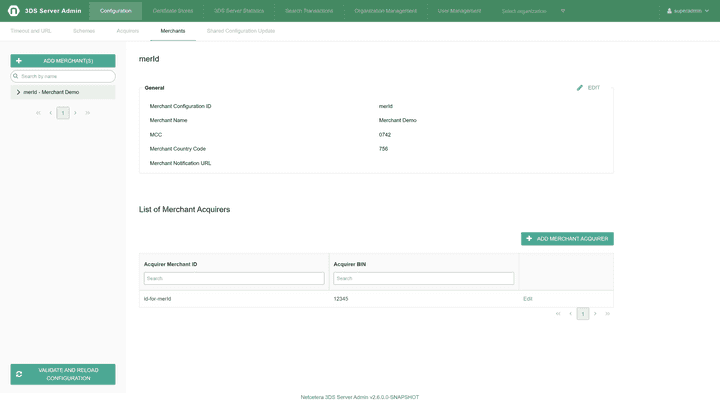
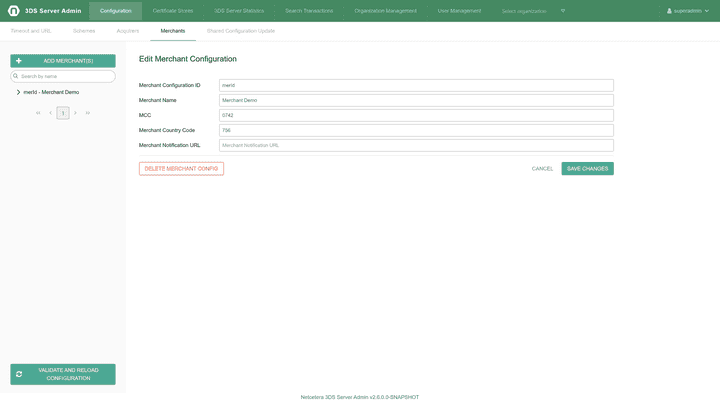
Edit Merchant:
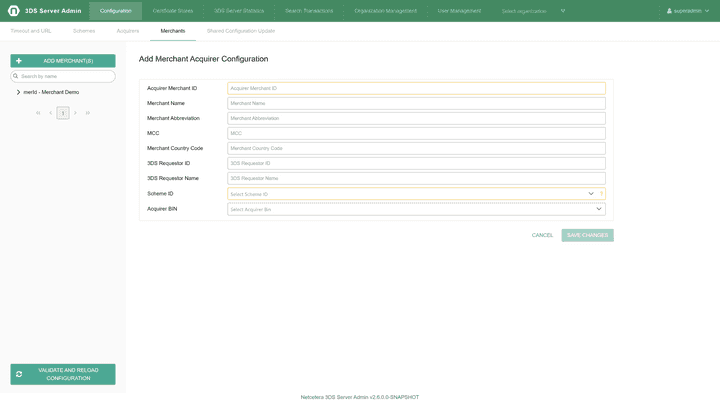
Add Merchant Acquirer:
View Merchant Acquirer:
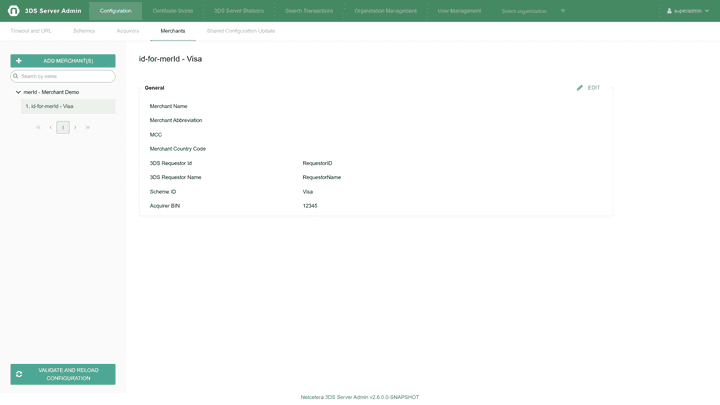
Edit Merchant Acquirer:
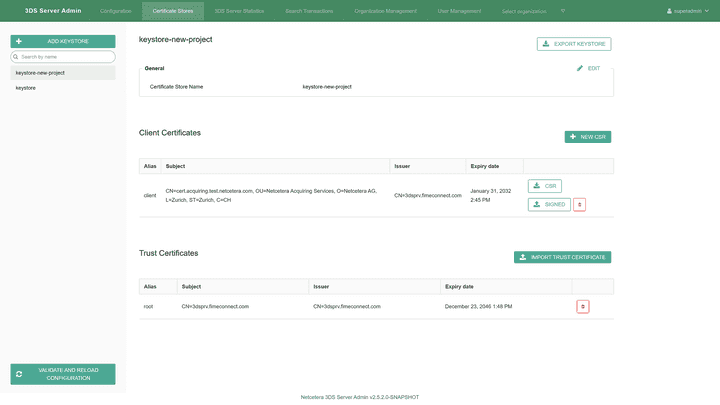
Certificate Stores configuration
The Certificate Stores tab allows configuration of the client and trust certificates.
Adding certificate store in Java KeyStore (JKS) format
The Add keystore button allows importing certificate store by entering the certificate store name, certificate store password and uploading the certificate keystore in Java KeyStore (JKS) format.
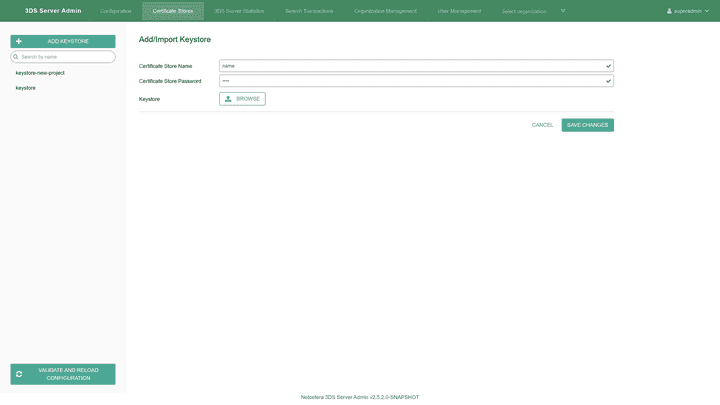
Creating empty certificate store
The Add keystore button allows creating empty certificate store by entering a certificate store name and password, without selecting a keystore file.

Generating Certificate Signing Request (CSR) for an existing client certificate renewal
The Generate CSR for renewal button will download a Certificate Signing Request (certificate-alias.csr) file for an existing certificate renewal.
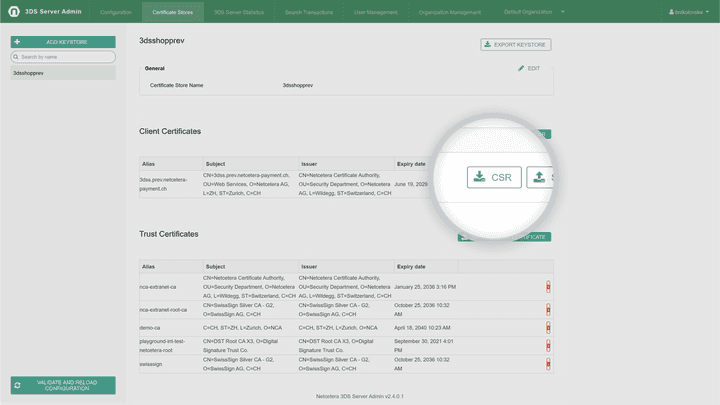
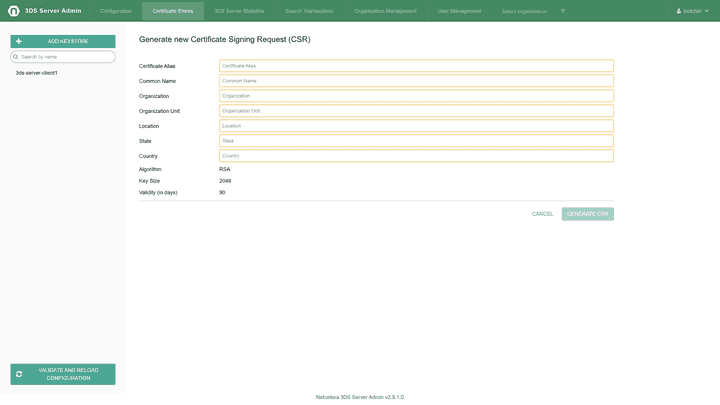
Generating Certificate Signing Request (CSR) for a new certificate
The Generate new CSR button will open a form requesting several certificate related information (Certificate alias, Common Name, Organization, Organization Unit, Location, State and Country) in order a new Certificate Signing Request to be generated. The algorithm for the CSR generation is always RSA with 2048 key size. The initial validity of the certificate is 90 days. Submitting the form will import an initial (not signed) certificate in the keystore and a Certificate Signing Request for it will be downloaded.
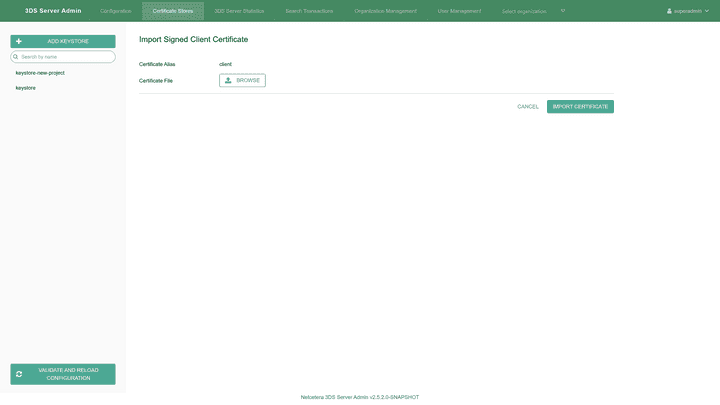
Importing signed certificate in the certificate store
Once a CSR is signed by a Certificate Authority (CA), the signed certificate can be imported in the keystore by clicking the Import signed certificate button. A signed certificate can be imported for an already existing certificate alias or a new one. The certificates that were used to sign the certificate (CA certificate, root CA certificate and/or any in between in the certificate chain) should be imported as trusted before importing the signed client certificate.
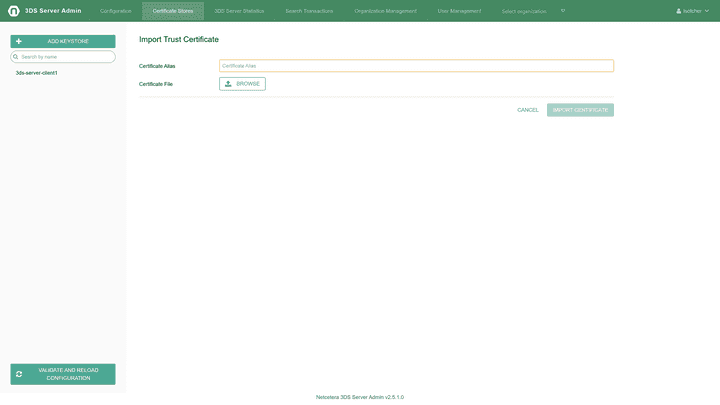
Importing trust certificate in the certificate store
By clicking the Import trust certificate button a trust certificate can be imported in the keystore.
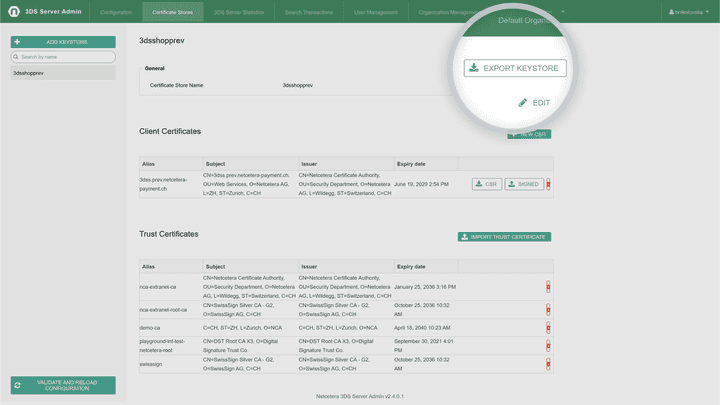
Exporting certificate store in Java KeyStore (JKS) format
The Export Keystore button will export the certificate store in Java KeyStore (JKS) format.